What Is Secure Payment Processing?

Every MSP knows how important client trust is. But what many don’t realize is that the trust you work to build through great service and communication can be undone in seconds by a compromised payment.
That’s exactly why secure payment processing should sit at the core of your business strategy. When your payments are secure, your MSP runs smoothly, scales steadily, and maintains healthy client relationships. When they’re not, everything (from cash flow to client trust) starts to break down.
As payment fraud continues to surge across the U.S. with losses topping $16.6 billion in 2024, understanding how money moves (and where it can be intercepted) has become just as essential for MSPs as managing firewalls or patching servers. The same attention you give to client network security now needs to extend to your own financial operations.
In this article, we’ll look at what defines a truly secure payment system today, how to keep your own payments safe, and also how to guide your clients toward the same standard.
How Cybersecurity Changed the Payments Game and Why MSPs Are in the Crosshairs
The shift to digital payments brought speed, convenience, and automation, but it also opened new doors for attackers. Every online portal, emailed invoice, or stored card detail represents another point of vulnerability that malicious actors can exploit.
According to the 2025 AFP® Payments Fraud and Control Survey, 79% of organizations reported payment fraud attempts or attacks in 2024. Check fraud remains the leading form (reported by 63% of organizations), but digital fraud attempts are becoming more targeted and growing more sophisticated every year.
For MSPs, that risk is magnified. MSPs sit at the intersection of technology, finance, and trust, managing not just their own payments but also the systems and data of multiple clients. That makes them a high-value target and a potential gateway for further downstream attacks. If one MSP’s payment process is compromised, every connected client could become vulnerable in a matter of hours.
There are a few reasons MSPs face such heightened exposure:
- Recurring billing cycles: Monthly or quarterly invoicing creates a predictable pattern that attackers can study and exploit. Once they identify a payment cadence, they can intercept or spoof legitimate requests with alarming precision.
- High transaction volume: Many MSPs process hundreds of invoices per month. That scale makes it easy for subtle discrepancies or fraudulent transfers to slip through unnoticed until real damage is done.
- Stored client data: MSPs often maintain sensitive account details for recurring billing, which can be used in credential-stuffing or phishing attacks to impersonate legitimate payment instructions.
When you’re handling both your own payments and your clients’ financial touch points, every transaction becomes a potential entry point.
That’s why payment security isn’t just about preventing cash loss, it’s about protecting trust loss.
What Makes a Payment “Secure”?
A secure payment protects both the payer and the payee at every stage, from initiation and authorization all the way through settlement and recordkeeping. The goal is to move money efficiently, but also in a way that prevents interception, impersonation, or alteration.
In action, an insecure payment process may look something like this:
An MSP emails an invoice to a client. The client confirms. But before the payment arrives, the email thread is intercepted by a malicious actor who changes the address or replaces the attached invoice with one that routes funds elsewhere. To the client, everything looks normal…they recognize the sender’s name, the invoice number, or even the logo. But by the time the MSP realizes the check never came, the payment has already cleared into a criminal account.
On the other hand, here are the key elements that define a secure transaction:
- Data Encryption: All financial details (account numbers, routing information, or card data) are encrypted end-to-end. That means even if a transmission is intercepted, the information is unreadable to anyone without the proper decryption key. Modern systems use advanced encryption standards to safeguard every byte of payment data.
- Authentication and Verification Layers: Secure payment systems don’t rely on trust alone. For instance, when setting up ACH, micro-deposits or real-time account validation ensure the bank details actually belong to the intended party before any funds move.
- Traceability and Auditability: Every legitimate payment leaves behind a verifiable record. This digital paper trail allows for real-time monitoring, fraud detection, and faster dispute resolution. If a transaction ever looks suspicious (wrong amount, unusual timing, mismatched IP) it can be traced and flagged immediately.
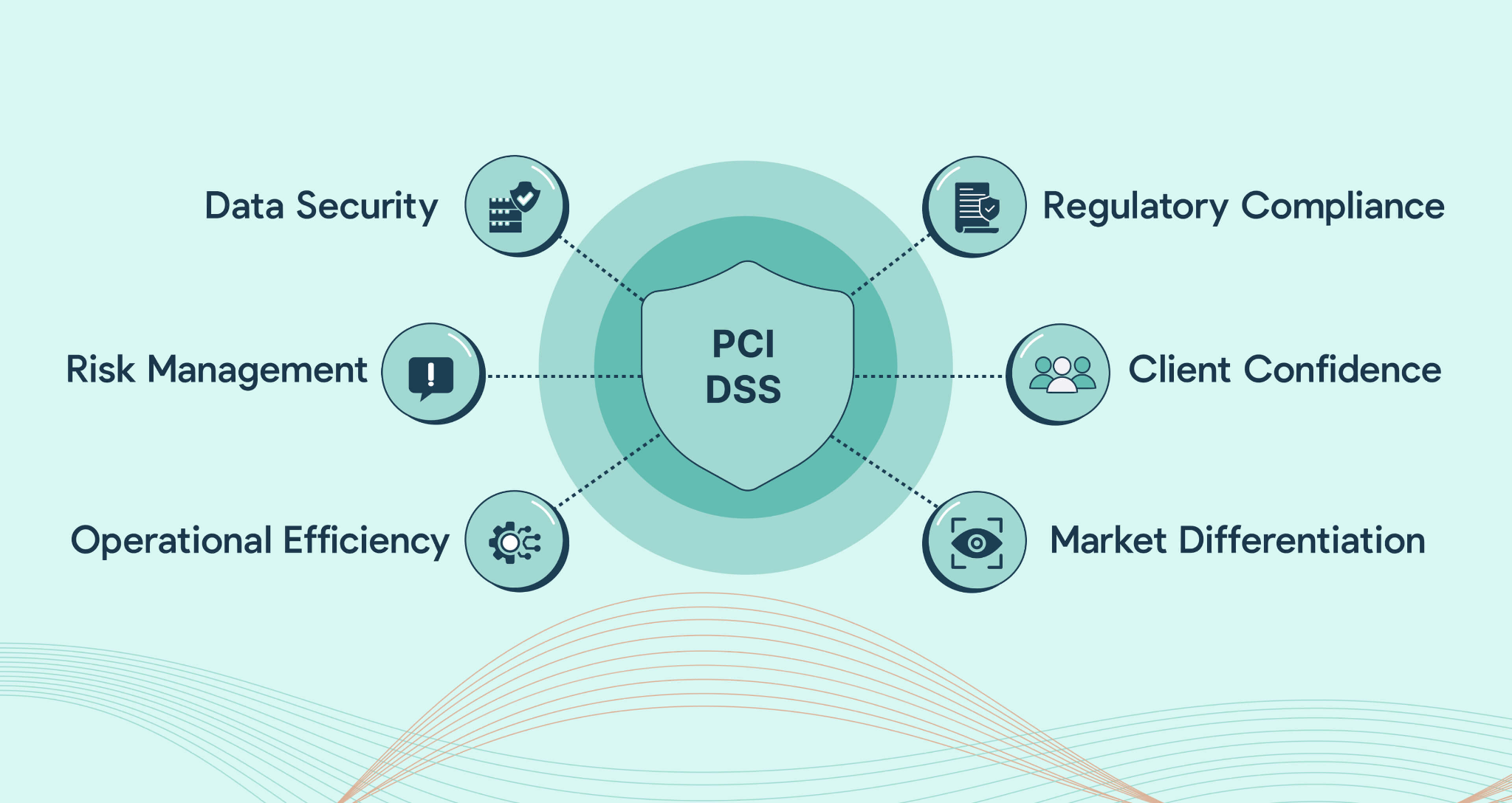
- Regulatory and Compliance Standards: Secure systems operate under strict frameworks (like PCI DSS for card data and NACHA for ACH) that require ongoing audits, access controls, and validation protocols. These standards ensure every process around security (from data storage to user access) is continually monitored and compliant.
When these layers work together, fraud attempts become exponentially harder to execute and far easier to detect.
The Most Secure Payment Methods for MSPs
There’s no shortage of ways to move money, but not all are built for security. For MSPs, the most reliable methods combine encryption, verification, and automation without adding friction for clients.
Among modern payment options, ACH stands out for its balance of safety, speed, and simplicity. Each transfer moves directly between verified bank accounts, avoiding the exposed data, third-party gateways, and manual handling that make checks and cards more vulnerable. Every transaction follows NACHA’s strict verification and compliance framework, giving you a predictable, auditable flow from initiation to settlement.
FlexPoint builds on that foundation with Same-Day ACH, automated billing, and layered protection. Every payment passes through account validation, risk scoring, and anomaly detection, ensuring suspicious activity is caught early. The result? Secure, same-day deposits with less manual follow-up and fewer surprises.
For a deeper comparison of ACH vs. credit cards and checks, check out our article: ACH, Credit Cards, and Checks: Which Is the Most Secure Payment Method?
4 Steps to Secure your Payments
Even with advanced technology, payment security ultimately depends on consistent practices. Whether your MSP already uses digital payments or still accepts paper checks, building resilience into your payment workflows is what prevents small mistakes from becoming major breaches.
Here’s how to strengthen your payment security posture without adding friction to your operations:
1. Use verified, encrypted platforms
Not all payment tools offer the same level of protection. While it may be tempting because of ease of use or familiarity, avoid basic or consumer-focused apps, like standard PayPal personal accounts, Venmo, or unverified ACH transfer services, since they lack enterprise-grade security.
Make sure to do your due diligence before selecting a billing platform. And always process transactions through PCI-compliant or NACHA-certified systems, like FlexPoint, which encrypts every payment end-to-end and applies layered verification before funds are released.
The best platforms actively monitor and score transactions for risk, flagging suspicious activity in real time so potential fraud never reaches your books. Using verified, secure platforms is essential for protecting your business and your clients.
2. Don’t store payment data locally
It’s tempting to keep client card numbers or bank details on file for convenience, but that’s one of the most common and costly mistakes MSPs make. Local storage (whether it’s in an Excel spreadsheet, CRMs, or internal databases) creates unnecessary exposure and increases the risk of accidental leaks or breaches.
Instead, use a trusted payment processor that manages tokenization and encryption for you. Tokenization replaces sensitive payment data with randomly generated identifiers, and encryption ensures those details remain unreadable in transit or at rest. Together, they eliminate the need for your team to ever handle or store raw financial data directly.
With FlexPoint, sensitive payment information never touches your internal systems. We help you stay secure and compliant in many ways. Transactions are encrypted end-to-end, validated through multiple security layers, and managed in compliance with industry standards like PCI DSS and NACHA, making it far easier for your MSP to maintain security without extra overhead.
3. Train your team and clients on payment fraud tactics
While your EDR software and email filters can block most automated threats, humans remain the first line of defense. Many payment breaches start with phishing emails, spoofed invoices, or domain impersonation which are tactics that exploit trust rather than technical flaws.
Make sure your staff and clients both know what to look for. Regularly remind clients to verify payment instructions, confirm the sender’s domain, and double-check any unexpected requests to change payment details. Even a single misrouted payment can cause major disruption for both sides.
Generic billing tools like QuickBooks make this harder, since their payment links, emails, and invoice branding all originate from standard Intuit domains that are easy for attackers to spoof. FlexPoint eliminates that weak spot entirely. Every MSP using FlexPoint gets a branded payment portal with a custom domain, emails that come from your company’s address, and a secure client portal with SSO. This creates a trusted, recognizable environment for clients to verify and complete payments safely, removing the uncertainty and guesswork that often lead to fraud.
4. Encourage clients to adopt ACH
The biggest vulnerability in your payment process often isn’t your system—it’s your clients’ habits. Many still rely on paper checks or unsecured email-based payments simply because that’s what they’ve always done. Helping them modernize how they pay you protects both sides from unnecessary risk.
Start by moving clients away from checks and email-based payments toward a secure client payment portal. When payments are centralized in one verified environment, clients always know where to go, and you can confidently track every transaction. FlexPoint makes this easy with a branded payment experience—clients receive invoices from your domain and pay through your secure portal, not a generic processor link. That simple shift eliminates the spoofed emails, fake invoices, and lost-in-the-mail payments that cause most payment delays and fraud incidents.
From there, guide clients toward ACH as their default payment method. ACH is not only faster, but inherently more secure. Payments move directly between banks under NACHA’s oversight, with no exposed card data or manual entry. Businesses using ACH as their primary method consistently report lower fraud exposure than those relying on checks or cards.
With FlexPoint, clients can pay via ACH in just a few clicks from a secure invoice link or within the portal. It’s easier for them, safer for both parties, and better for your bottom line.
Tip for implementing: Secure payments don’t happen by chance, they’re built through layered systems, smart tools, and clear communication. It’s not enough to have secure technology; your clients need to know how and where to use it safely.
Make sure they understand your payment process end to end: where to pay, what legitimate invoices look like, and how you’ll communicate payment requests. For example, you should never ask clients to pay via a new link or account without verifying through multiple channels like a quick call or confirmation through your client portal. Some MSPs even establish a shared “code word” or passphrase for payment verification, adding another layer of trust to high-value transactions.
By pairing strong systems with consistent communication, your MSP can drastically reduce fraud risk while improving both cash flow and client confidence.
The Security Case for Moving to ACH
Security is the backbone of long-term client trust and financial stability. Which means that for MSPs, adopting ACH payments is both a method to prevent fraud while simultaneously building a steady foundation for faster and more sustainable growth with lower overhead and friction. But it’s also understandable if asking your clients to make a change ruffles feathers. That’s why it helps to clearly understand the security case for ACH so you can confidently address their questions.
ACH gives MSPs and clients what checks and cards can’t: speed, control, and security. With ACH, payments move securely between banks. With Same-Day ACH, funds clear the very same day clients send them, eliminating the guesswork and delays of paper checks or card settlements on both sides. Faster cash flow means more reliable operations, simpler forecasting, and fewer liquidity gaps between billing cycles for you and more independent, safer, and happier clients.
Beyond protection and speed, Same-Day ACH with FlexPoint saves both time and money. You avoid the 2–3% processing fees of credit cards (and your client avoids any surcharges imposed to cover them) and the manual burden of mailing, tracking, and depositing paper checks. FlexPoint’s automated billing and reconciliation reduce administrative strain while improving accuracy.
The Bottom Line
MSPs cannot approach secure payment processing as just another box to checkSecure payment processing is what ensures your business lasts and grows. The stakes are high, and without it, running an MSP is impossible. Every transaction represents not just revenue, but the confidence your clients place in your business. A single misstep can ripple outward quickly, disrupting cash flow, damaging relationships, and putting your reputation on the line.
At its core, secure payment processing combines encryption, layered verification, traceability, and compliance to ensure that every transaction is authenticated, auditable, and resilient against fraud. It’s what separates a billing workflow that simply “works” from one that actually protects your business and your clients.
When your payments are secure, your MSP scales confidently, your cash flow stays steady, and your clients remain confident that their money is in safe hands.
With FlexPoint, every transaction is verified, traceable, and protected, so your MSP can focus on growth and client relationships, not chasing errors or worrying about fraud.
Take a tour of FlexPoint today and turn secure payment processing from a challenge into a competitive advantage. And if you're still accepting the most unsecured payment method today (paper checks) but are overwhelmed by the work it will take to transition away from them, we've already done half the work for you. Get the Moving Clients Away from Checks Toolkit for free!







.png)