Common Payment Security Risks (and How to Avoid Them)

Payment security matters for every business, but it’s critical for MSPs.
Unlike storefronts where transactions happen face-to-face, most MSPs deliver services and collect payments remotely through portals, invoices, or automated billing platforms. That structure introduces both opportunity and risk. On one hand, it’s efficient and scalable; but on the other, it is also more exposed to error, fraud, and system compromise.
Because MSPs handle both their own billing and sensitive client systems, attackers see them as high-value targets: compromise one MSP, and you can reach dozens of downstream businesses. And a single weak link in your financial operations (whether it’s a spoofed invoice, a lost paper check, or an unverified portal login) can put your whole business at risk, not just your cash flow.
This article breaks down the most common payment security risks facing MSPs today and what you can do to avoid them before they cost you time, money, or client trust.
Phishing & Business Email Compromise (BEC)
One of the most common ways payment fraud starts is with a spoofed email which can include: a fake invoice, a vendor request to change bank details, or a login prompt to your payment portal.
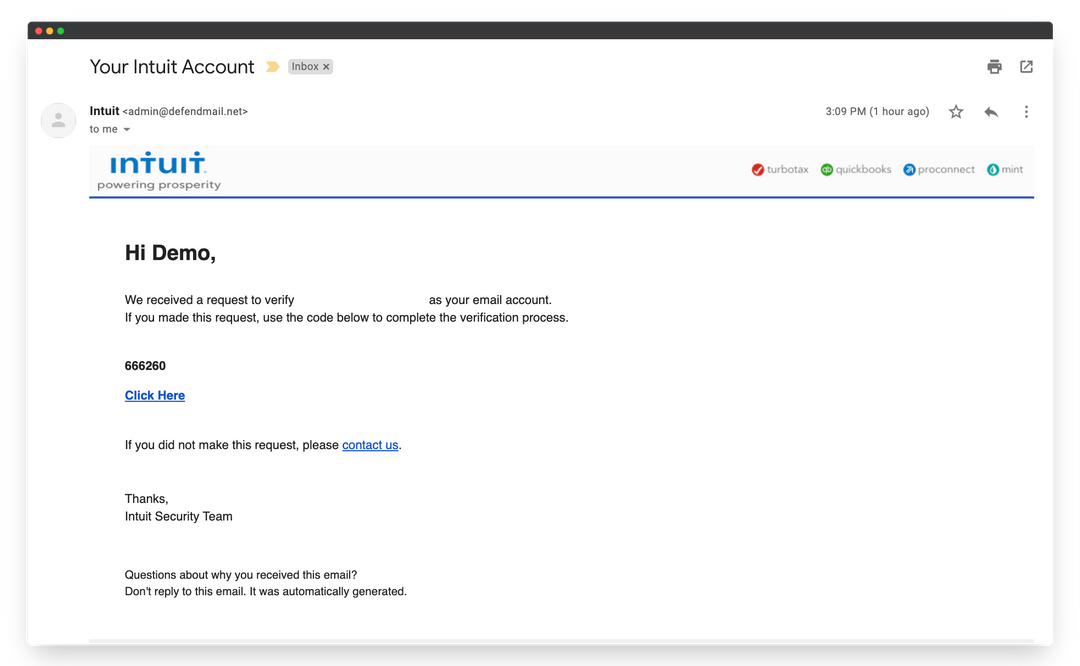
For example, QuickBooks invoices are sent from generic Intuit domains, which are easy for malicious actors to mimic. From your client’s perspective, it’s nearly impossible for them to tell the difference at a glance. And even though fraud that occurs on this level may not be your fault, it will reflect on your MSP which may cost you in client relations.
A few studies highlight the severity and regularity of this kind of risk: phishing and BEC attacks accounted for 73% of all reported cyber incidents in 2024. And with the rise of AI, these emails are becoming increasingly convincing and common.
The total losses reported to the Internet Crime Complaint Center (IC3) in 2024 were $16.6 billion, many being the result of BEC.
What you can do as an MSP owner is establish strong payment verification practices both internally and with your clients. Always confirm payment instruction changes through multiple communication channels (never rely on a single email). Encourage your clients to bookmark your verified payment portal and remind them: if they ever receive an unexpected invoice or link, they should confirm it directly with your team first.
A secure payment platform can do much of the heavy lifting here. Combined with regular communication and phishing awareness training, this makes it exponentially harder for impersonation attacks to succeed.
Insecure Payment Portals
Research shows that payment portals without proper encryption, authentication, or tokenization are among the most commonly exploited points of entry for fraud. Misconfigured SSL/TLS certificates, outdated APIs, and unverified links all open the door for data interception and credential theft.
According to the Verizon 2024 Data Breach Investigations Report, over 70% of breaches in SMBs stemmed from web application vulnerabilities, including insecure payment pages and credential misuse. In fact, 75% of cyberattacks start with stolen credentials, often taken from poorly secured or outdated websites.
For MSPs, this matters deeply because payment systems often live within the same infrastructure as technical service platforms.
Because of this, you’ll want to take a close look at any payment portal you are currently using. It may seem small, but it is critical that it enforces MFA and device verification. Without multi-factor authentication, anyone with stolen credentials can log in as a client or staff member and initiate payments, refunds, or access stored billing data. Once that happens, it’s almost impossible to prove which activity was legitimate.
Even secure portals and encrypted storage can be undermined when authentication and verification fall short. Attackers routinely exploit single-factor logins, reused credentials, and weak account validation to gain access. You might still be using a familiar payment portal out of convenience, but if it doesn’t enforce MFA, device verification, or tokenization, your MSP and your clients are left vulnerable to attack.
Because of that, MSPs need verified, encrypted payment environments that clients can trust and use consistently. Implement a secure payment portal and your clients will always know when to pay and they will be safe while doing so.
Poor Storage Practices
Storing client payment data in spreadsheets, CRMs, or legacy billing systems may feel efficient, but it’s one of the most underestimated risks for MSPs. Payment systems are only as secure as their weakest link, and when sensitive data like account numbers or card details live on local servers or shared files, every user who can access them becomes a potential threat and target.
In practice, poor data storage isn’t always about malicious intent, it’s often about misconfiguration, overexposure, or convenience.
59% of incidents involving internal actors stem from system misconfigurations or data mishandling, not direct hacking. For MSPs, that risk is amplified by scale: you’re managing financial workflows for dozens of clients and likely have multiple technicians and employees with access to vulnerable information.
Poor storage practices for payment security often look like this:
- Unencrypted records: Card or routing numbers stored in plain text files, CSVs, or non-tokenized CRMs.
- Improper access controls: Admin privileges or shared logins that allow too many people to view or export sensitive data.
- Legacy integrations: Older PSA or billing systems that don’t meet modern PCI DSS or NACHA data handling requirements but still sync or log sensitive payment fields.
- Unsecured backups or exports: Payment data stored in offsite drives or cloud folders without encryption or access monitoring.
Since poor data storage is seen as the fault of the MSP and not a malicious actor, you will be held responsible which could result in additional fines. PCI DSS violations alone can result in fines ranging from $5,000 to $100,000 per month depending on the scope and duration of noncompliance.
The solution here isn’t just to “store securely”, it’s to minimize what you personally handle in the first place. Modern payment platforms eliminate the need for internal data handling altogether. Through tokenization, encryption, and secure vaulting, payment details never touch your systems. Instead, each transaction is handled end-to-end within a compliant, monitored environment, which keeps you focused on service delivery, instead of worrying about data exposure.
Paper Checks
Cybersecurity breaches aren’t the only risks facing MSP payments, though. A massive payment security risk lives in the association with MSP owners and their clients that “paper checks” are secure because they’re not vulnerable to cyber fraud. So even if your online systems are fully secure, accepting paper checks means reintroducing risk into a process you’ve otherwise locked down.
But in reality, checks are one of the most fraud-prone payment methods in use today. Every paper check contains a trove of sensitive data: client names, routing and account numbers, and even signatures printed in plain view. Once that check leaves your client’s home, it passes through dozens of touch-points: mail carriers, sorting centers, receiving desks. Since the pandemic, incidents of check fraud have surged over 385% nationwide, and the U.S. Postal Service continues to warn about organized theft rings targeting business mail for this exact reason.
At any one of those steps, it can be stolen, altered, or “washed” and reused by malicious actors.
The 2024 AFP® Payments Fraud and Control Survey found that checks remain the most-targeted payment method for fraud, with 63% of organizations reporting incidents.
For MSPs, the risk of paper checks is amplified: recurring payments mean recurring exposure.
Checks aren’t just slow, they’re fundamentally insecure. In a digital-first environment, paper payments expose your business and your clients to unnecessary risk that no modern MSP should carry.
If you’re ready to move away from the riskiest payment method but are unsure where to start, learn how to transition from paper checks to secure digital payments, without disrupting your clients or cash flow.
Best Practices: How to Strengthen Payment Security
Payment security comes down to strong systems and consistent habits. Here are five proven ways to keep your clients’ payments secure and your operations protected:
- Use verified, encrypted platforms. Always process payments through PCI-compliant or NACHA-certified systems that encrypt every transaction end-to-end and apply layered verification before funds move.
- Avoid storing payment data locally. Never keep raw account or card information in CRMs, spreadsheets, or shared drives. Instead, rely on processors that handle tokenization and encrypted storage, so even if data is intercepted, it’s unreadable.
- Strengthen authentication and verification. Implement multi-factor authentication (MFA), validate bank details with micro-deposits or real-time verification, and ensure access to billing systems follows least-privilege principles or make sure you use a tool that does.
- Train your team and clients to recognize fraud attempts. Most breaches begin with phishing or spoofed invoices. Regularly educate both employees and clients to confirm payment requests via trusted channels and to never act on unverified emails.
- Automate reconciliation and real-time alerts. Automated tools that flag unusual activity, mismatched invoices, or failed transactions can prevent small anomalies from turning into serious financial losses.
Curious about other best practices in smoothing and securing your client’s payments? Read more here: The Ultimate Guide to MSP Payment Best Practices: Ensuring Smooth and Secure Transactions.
Turning Payment Security Into a Competitive Advantage
For MSPs, payment security isn’t a side concern, it’s the foundation of everything you do. When you manage both client infrastructure and financial workflows, even a single compromised transaction can snowball far beyond your own balance sheet. According to industry data, the average SMB loss per cyberattack is roughly $25,000, but for MSPs, the real cost is multiplied by downtime and the loss of client confidence.
Every risk in this article has one thing in common: they thrive where systems or communication break down. The good news is that each can be prevented with the right combination of tools, processes, and awareness.
By using verified, encrypted platforms, enforcing strong authentication, minimizing what data you handle internally, and training both your staff and your clients to spot red flags, you dramatically reduce exposure.
If you’re ready to simplify and secure the way you get paid, platforms built specifically for MSPs like FlexPoint combine automation, encryption, and account verification to keep your payments fast, predictable, and protected. Watch an on-demand demo here!







.png)